House Of Kiwi

House of kiwi
在vnctf2022的一道题目的官方wp中发现该方法,遂学习
使用场景
- 能够触发
__malloc_assert,通常是堆溢出导致 ;触发__malloc_assert一般改topchunk的size和prev_inuse - 能够任意写,修改
_IO_file_sync和IO_helper_jumps + 0xA0 and 0xA8
1 | __malloc_assert (const char *assertion, const char *file, unsigned int line, |
使用方法
实现进入assert后,可以想到fflush和fxprintf都和IO有关,可能需要涉及IO,一步步调试看看可以发现在fflush函数中调用到了一个指针:位于_IO_file_jumps中的_IO_file_sync指针,且观察发现RDX寄存器的值为IO_helper_jumps指针,多次调试发现RDX始终是一个固定的地址 。
即利用方法为 通过修改 _IO_file_jumps + 0x60的_IO_file_sync指针为setcontext+61修改IO_helper_jumps + 0xA0 and 0xA8分别为可迁移的存放有ROP的位置和ret指令的gadget位置,则可以进行栈迁移
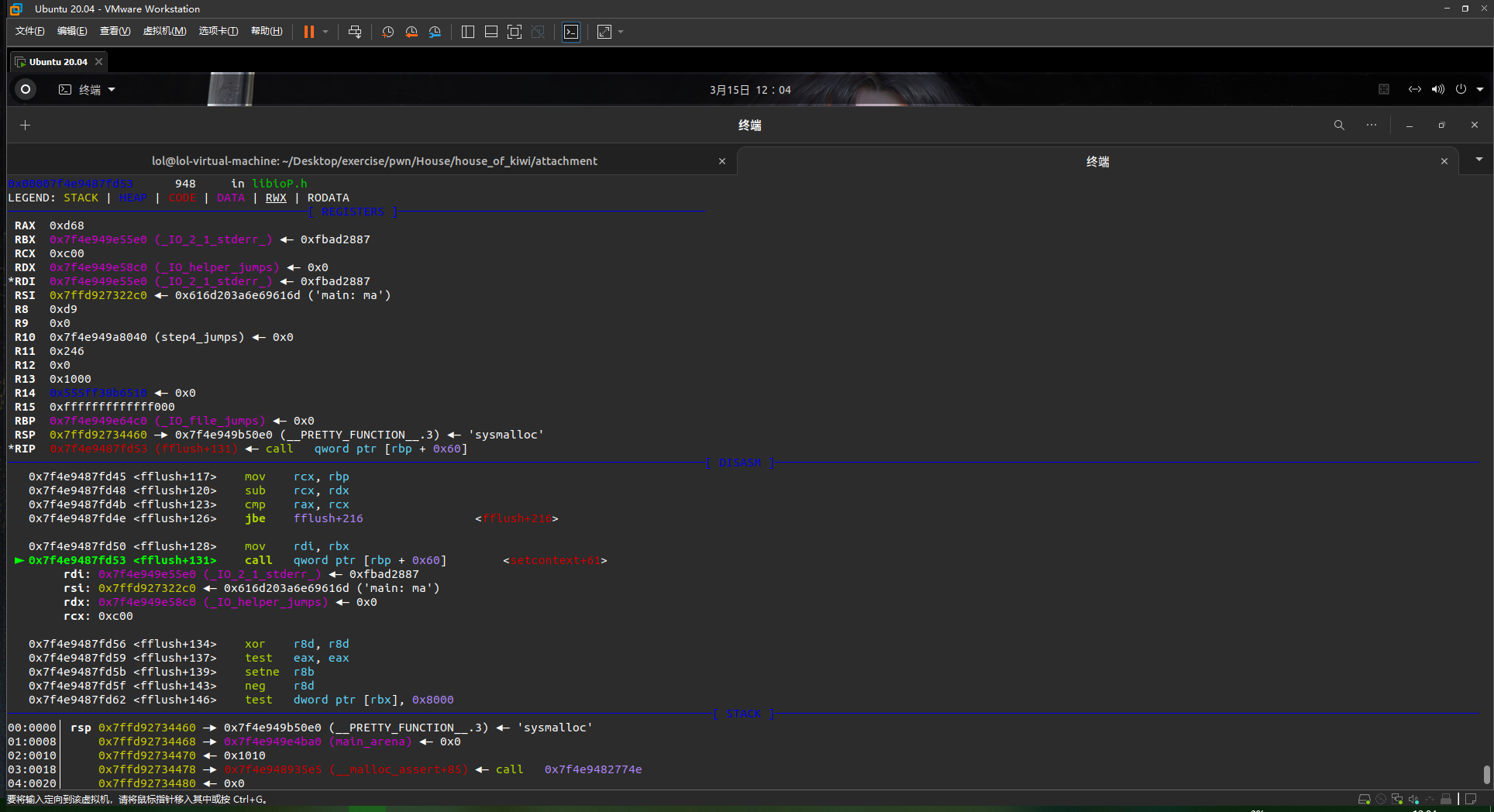
上图是最后进入了malloc_assert中的fllush中,在该函数中最后会调用qword ptr [rbp+0x60],而这里rbp是_IO_file_jumps,这里设置为setcontext+61,而后后面的参数可以看情况利用,但是rcx要设置为最后srop的地址
demo
1 | // Ubuntu 20.04, GLIBC 2.32_Ubuntu2.2 |
例题: NepCTF 2021年中NULL_FxCK
比赛笔者没有参加,但是在面试V&N的时候,最后问到我对于2.31版本下的off-by-null与2.23版本有什么不同,当时还没掌握,然后wjh大佬就给了这道题同时给了3天时间
1 | #!/usr/bin/env python |
- 本文标题:House Of Kiwi
- 本文作者:LOLOLO
- 创建时间:2022-03-11 16:30:19
- 本文链接:https://lololo-pwn.github.io/2022/03/11/House-Of-Kiwi/
- 版权声明:本博客所有文章除特别声明外,均采用 BY-NC-SA 许可协议。转载请注明出处!
评论